You're probably familiar with Amazon's web services, but how about their security? For a long time, it was only available to business customers. However, Amazon recently opened up its cloud-based security features to everyone. They're calling this "Amazon Security Lake." Quite a catchy name, right?
Let's see what it has brought to us in terms of security.
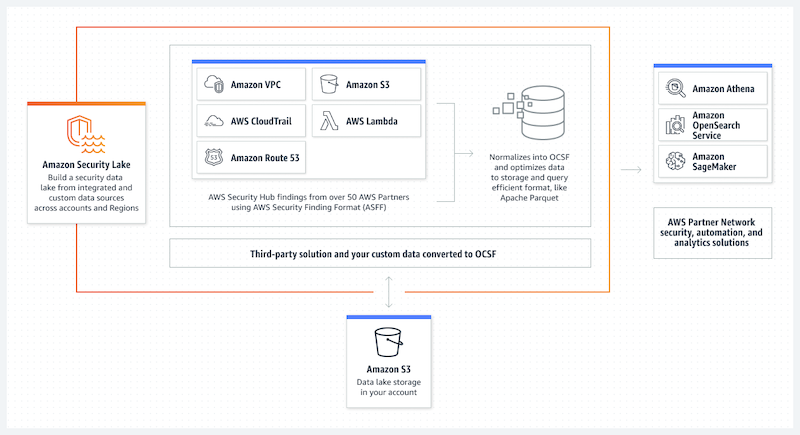
Amazon Security Lake is a global repository of security best practices, standards, and guidelines available to all customers. It is a resource for building secure applications and evaluating adversary threats, and it enables customers to identify potential security problems before they impact their business.
In addition, Amazon Security Lake provides automated threat detection capabilities based on the data in the lake. You can use these capabilities to monitor your environment for attacks or suspicious activity, such as API calls or network flows that indicate an intrusion attempt.
Security Lake maintains the data lifecycle with tuneable retention and replication settings. It automates collecting security-related log and event data from AWS and third-party interconnected services. The Open Cybersecurity Schema Framework is a standard open-source schema that Security Lake translates imported data to (OCSF).
Other AWS services and third-party services can subscribe to Security Lake's data for incident response and security data analytics.
Amazon Security Lake Brings New Opportunities
Vectra AI introduced a platform compatible with the recently released Amazon Security Lake on November 29. After a quick setup process, Security Lake is compatible with Vectra Cloud Detection and Response.
"As cyberattacks increase in volume and intensity, clients need ecosystem solutions that simplify security processes while addressing real threats across global networks," said Sachin Saranathan, director for cloud and technology alliances at Vectra.
According to Wallace,
"Cloud security data combined with on-premises data is consolidated into an Amazon Security Lake, a customer-owned data lake."
Customers can make their logs accessible to solve a wide range of security use cases, including threat detection, investigation, and incident response, with the "Vectra Security Findings" feature in Amazon Security Lake.
The following are some key benefits that Amazon Security Lake will bring to market:
Amazon Security Lake for Multi-Cloud Solutions
Security Lake is built on top of the existing AWS infrastructure. Your existing applications can be migrated to Security Lake without changing their code or architecture. You can also use Security Lake to extend your current workloads across multiple clouds to operate more efficiently.
Analytics and Visualization
Amazon Security Lake provides a convenient way to visualize events, logs, and other data. This can be done through the Amazon Web Services (AWS) console or the Kibana application that allows users to analyze the data using Elasticsearch. Users can also create custom dashboards by using Kibana with Elasticsearch.
Time Series Database
Amazon Security Lake has a built-in time series database that makes it easy to store, query, and visualize time series data. This is useful for storing logs from IoT devices such as sensors and cameras.
Big Data Processing
Amazon Security Lake supports batch processing of large amounts of log data into more useful information by applying analytics algorithms such as anomaly detection on all incoming events and real-time analytics on streaming events.
AI and Machine Learning
You can use Artificial Intelligence (AI) algorithms such as anomaly detection, threat hunting, and behavioural analysis to detect suspicious patterns in user behaviour. Machine learning algorithms are used for automated incident response by analyzing historical data from your environment and detecting anomalies based on statistical models created from training data sets collected from previous incidents.
The Amazon Security Lake is a purpose-built data lake that automatically consolidates security data from the cloud, on-premises, and bespoke sources. Security Lake can offer a more holistic view of your company's security data. In addition, you may strengthen the safety of your data, apps, and workloads. Open Cybersecurity Schema Framework (OCSF) is now the industry standard thanks to Security Lake's adoption. With OCSF's help, the service can aggregate and standardize security data from AWS and other enterprise sources.
Use Cases
Amazon Security Lake allows you to:
Centralized Security Data for Consolidated Analytics
You can consolidate all your security data into a single repository for easy analysis with tools such as Amazon Athena, Amazon Redshift Spectrum, and Amazon QuickSight. You can also use AWS Lambda functions to automate the analysis of your logs.
Use Your Preferred Tools with Centralized Data
With Security Lake, you can use the tools you prefer to store and analyze the raw data from your systems, applications, and networks.
Examine Your Data with Custom Analytics
Security Lake's capabilities make it easy to run custom analytics on petabyte-scale data sets in seconds or minutes instead of hours or days. You can use these capabilities to detect anomalies or trends that could help identify potential threats faster than ever — without requiring additional training or resources.
Analyze Multiple Years of Security Data Quickly
You no longer need to worry about losing important information because it's stored in an environment that wasn't designed for long-term retention.
Secure Access to Your Data
Security Lake provides secure access over SSL/TLS connections through its web-based console or API interface. The console offers secure access to individual log files and aggregate views of log data across time and regions. The API provides fast access to the entire repository of data.
Features
Amazon Security Lake features include:
- Data Lifecycle Management and Optimization: You can define retention periods for your data so that Amazon Security Lake automatically deletes older data at specified intervals — saving you money on storage costs.
- Security Data Lake Access Management: You can control who has access to your data by setting permissions on tables, views, or schemas within Amazon Security Lake. You can also restrict access by location (region).
- Multi-Account and Multi-Region Support: You can use Amazon Security Lake for multiple accounts within one region or across multiple areas.
How to Access Amazon Security Lake?
Currently supported regions for Security Lake may be found at Amazon Security Lake Regions and endpoints. Reference the AWS service endpoints in the AWS General Reference for more information on Regions.
Each Region's Security Lake can be accessed in one of several ways:
AWS Command Line Interface (AWS CLI)
Use the command line interface of your computer to execute AWS and Security Lake commands with the AWS Command Line Interface. The command prompt offers a more efficient alternative to the console. If you need to create scripts to automate specific processes, the command line tools can help you out there, too.
AWS SDKs
Amazon provides several programming languages and platforms for building applications on top of Amazon Web Services (AWS). Each language or platform comes with an AWS Software Development Kit (SDK) that you can use to work with Security Lake directly from within your code base without writing any XML code or creating configuration files manually.
AWS Management Console
You can make and modify AWS assets using the AWS Management Console, a web-based tool accessible from any web browser. The Security Lake admin console is your gateway to all things Security Lake. The Security Lake console is where you'll do most of your work.
Security Lake API
The Security Lake API is everything you need to make secure HTTP requests to Security Lake programmatically.
Final Words
Amazon Lake Security Services is an excellent way to protect your cloud data. The service provides comprehensive security for log analysis and alerts that can detect malicious activity across accounts. It automatically identifies risky behaviour in AWS account activity logs and monitors AWS resources 24 hours a day, seven days a week.